DivvyCloud has published a report showing the extent of companies’ losses caused by errors in public cloud services configuration. We have studied this document and prepared an article to warn those at risk.
Data leakage happens for different reasons, but cloud misconfiguration has become the predominant cause of loss in recent years. Unfortunately, many organizations neglect cloud services’ security, even though customers, partners, and authorities rely on their discretion and professionalism when they entrust them with their data. An unsecured server and other errors in infrastructure settings are not reasonable excuses for data leakage.
Damage figures
33.4 billion records are leaked due to the misconfiguration of cloud services. According to a study by Ponemon Institute, the cost of one such recording for a company is $ 150. So, multiplied by the number of leaks, we get $ 5 trillion as of the total number of companies’ losses worldwide, which is only for the last couple of years.
According to a Gartner report, the public cloud services market in 2018 was $ 182.4 billion and $ 214.3 billion in 2019. It means that the companies’ loss due to cloud settings misconfiguration is more than 12 times the amount of investments in cloud services worldwide. Therefore, protecting your investments and preventing the costs of data leakage are the most important reasons why your clouds should be kept secure.
At the same time, the number of leaks caused by cloud services misconfiguration is 80% higher in 2019 than in 2018, and the companies’ losses demonstrate the same growth.
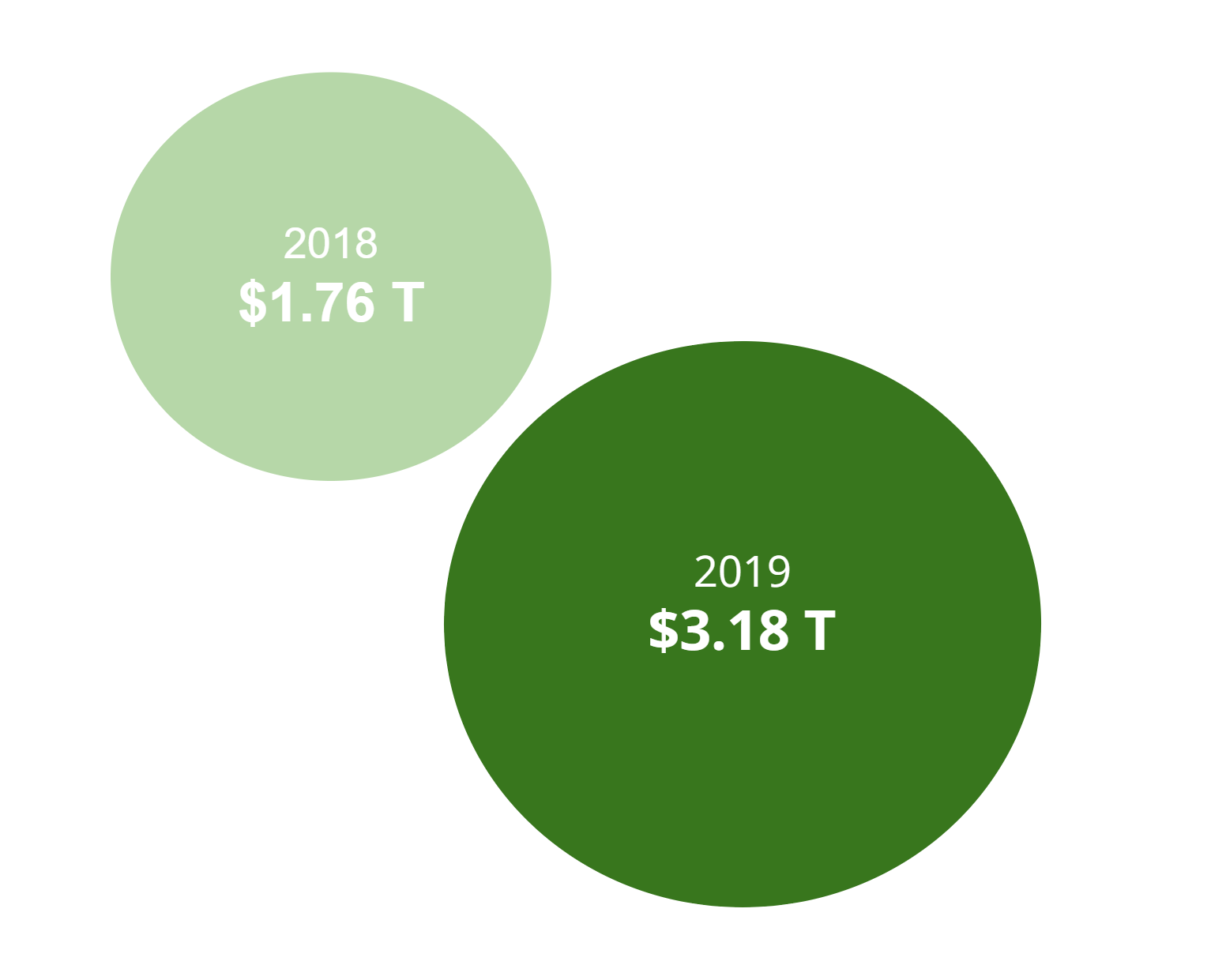
2018: 11.8 billion records were affected, aggregate loss costs $ 1.76 trillion.
2019: 21.2 billion records were affected, aggregate loss costs $ 3.18 trillion.
And these figures are probably not accurate: the McAfee report found out that 99% of cases of clouds misconfiguration are not reported, which means that the absolute number of leaks and the amount of loss they cause to companies is likely to be much higher.
Risk groups
Companies choose cloud services according to their speed and flexibility needs to keep them competitive in a fast-paced, innovative world but do not place a high priority on the implementation of appropriate security measures.
68% of companies recently affected by cloud misconfigurations were founded before 2010. This points to the fact that elder companies moving to cloud services find it more challenging to implement and maintain cloud security controls compared to younger companies who “were born in the cloud.”
Another risk factor is the situation of mergers and acquisitions of companies. For example, the 2018 Marriott / Starwood Leak is a remarkable example of how failing to do the right due diligence during a merger and acquisition can lead to significant security gaps.
The reason is a very complex procedure of secure merging of different companies’ IT infrastructures into an integral whole.
Such cases can have a negative impact on the value of the acquired company. For example, Verizon cut the total purchase price of Yahoo by $ 350 million when it was revealed that the data leakage at Yahoo, which occurred on the eve of the merger, was more significant than previously stated.
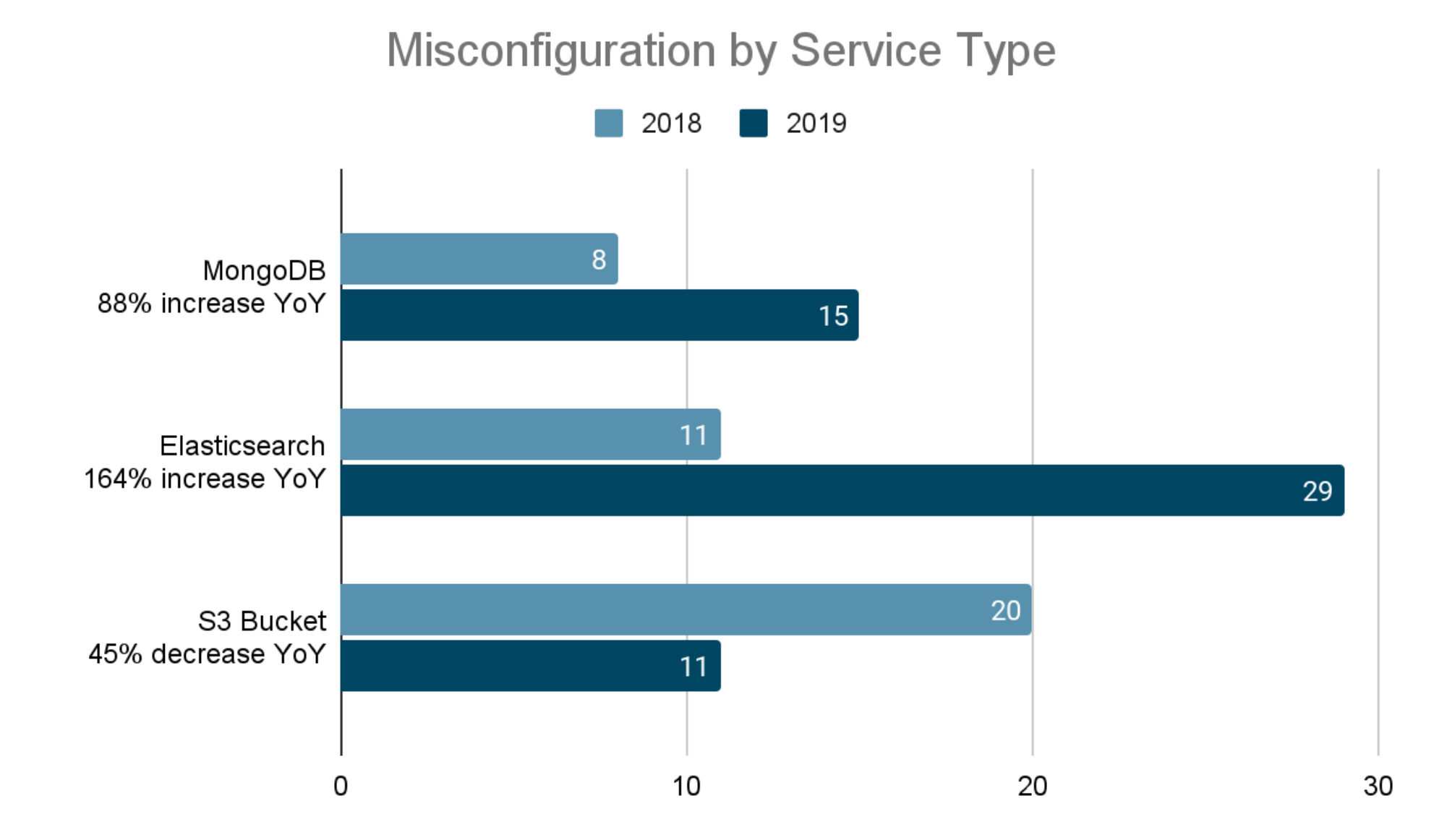
Also, the analysis of 196 episodes of data leaks caused by clouds misconfiguration found the services involved in each case and revealed the following:
- 44% of leaks examined in 2018 and 2019 were from Elasticsearch (a free software search engine used by sites such as Wikimedia, Quora, Foursquare, SoundCloud, GitHub, Netflix, Amazon, IBM, and others). In 2019, the number of leaks had tripled compared to 2018,
- 16% of leaks are caused by S3 Bucket (Amazon Object Storage). The number of leaks increased by 45% compared to 2018,
- 12% of leaks are from MongoDB (database). They were doubling leakage growth in 2019.
The most significant percentage of leaks occurs through AWS services. Still, while Microsoft Azure, Google Cloud Platform, and Kubernetes have reported few incidents, misconfiguration discredits the use of all cloud services.
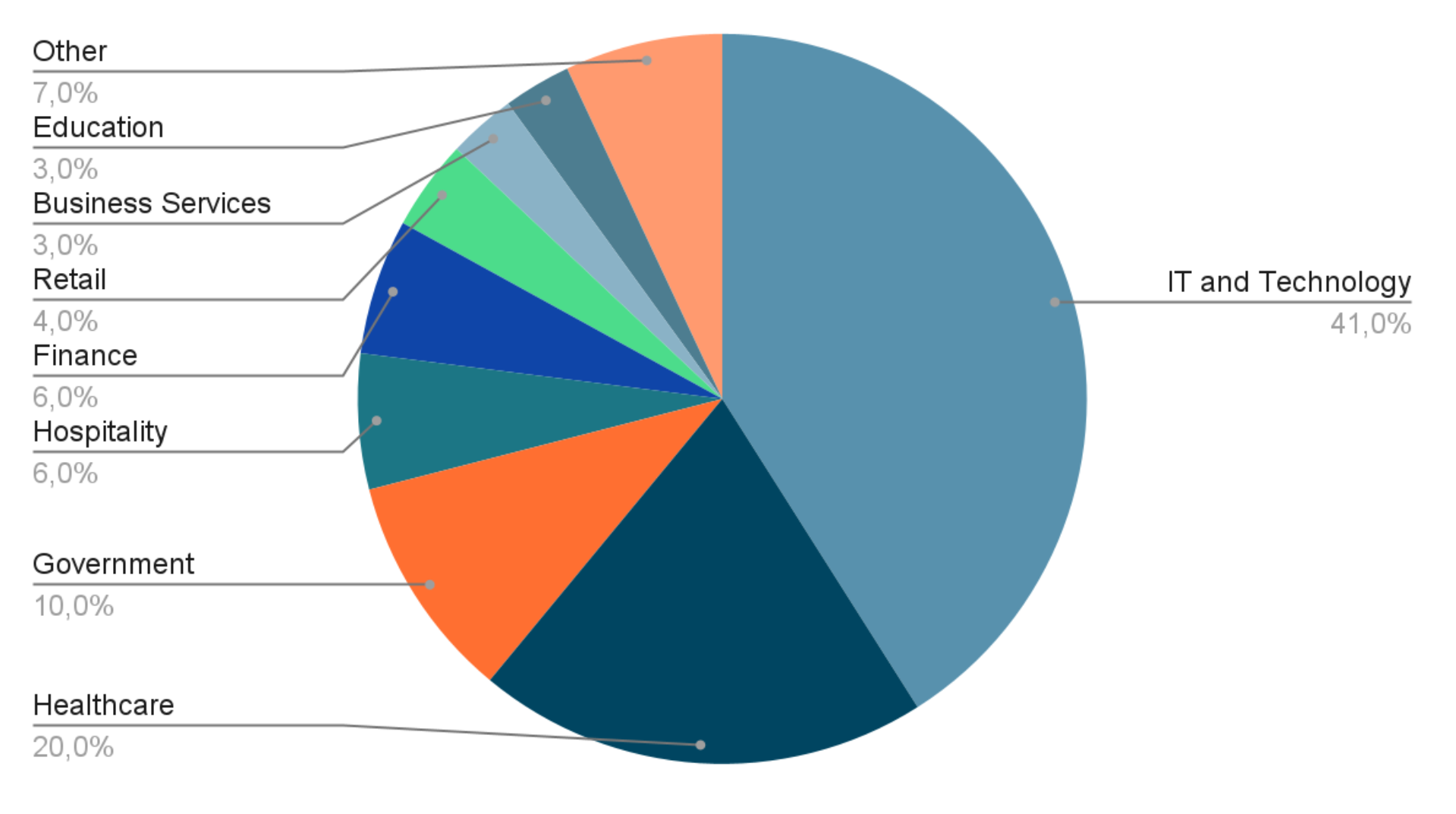
- 41% of leaks – Technological and IT companies,
- 20% of leaks – Healthcare,
- 10% Government,
- 6% of leaks each – Hospitality and Finance,
- 4% of leaks – Retail,
- 3% of leaks each– Education and Business Services,
- 7% of leaks – Other.
The cause of the problem
Cloud security is not always dependent on cloud service providers.
Gartner predicts that customers will cause 99% of misconfigurations in cloud security settings by 2025.
Companies are moving too fast adopting cloud services as they need to implement innovations to stay competitive. And only clouds can provide the flexibility and speed they need to do this.
The number of people using clouds is rising fast. Previously, an organization could have 40 people related to infrastructure. Today, it is usual for all 3,000 employees in a company to deploy applications and make configuration changes – a so-called continuous integration and continuous development approach. And these people don't even think about security when they deploy applications in their cloud infrastructure.
Many companies lack an integrated approach to infrastructure security, which is compounded by many inexperienced users and outdated cyber defense models. While the ever-changing nature of public clouds and container infrastructure is being mastered, risk control and risk minimization, account management, and compliance are often ignored. Unfortunately, these are the things that are no longer under the exclusive control of IT staff today.
Responsibility of the participants
When it comes to security, responsibility is shared between the customer and the provider. The customer is responsible for the way he uses the service, including proper settings of access control, storage, and computational performance, implementing the threat and protection analysis, and security of running applications and data processed in the cloud. This part of the client’s responsibility is often overlooked.
Providers, in turn, are responsible for providing security of the cloud service low-level components. This is a task they usually complete without issue. Contact only reliable IT service providers to reduce the risk of leakage due to misconfiguration of cloud services and strengthen your infrastructure’s protection. And to get rid of the tough call of administering your infrastructure in the data center, use the additional system administration and remote management services.


Comments